This is the blog section. It has two categories: News and Releases.
Files in these directories will be listed in reverse chronological order.
This is the multi-page printable view of this section. Click here to print.
This is the blog section. It has two categories: News and Releases.
Files in these directories will be listed in reverse chronological order.
This release is made possible with the support of NLnet foundation
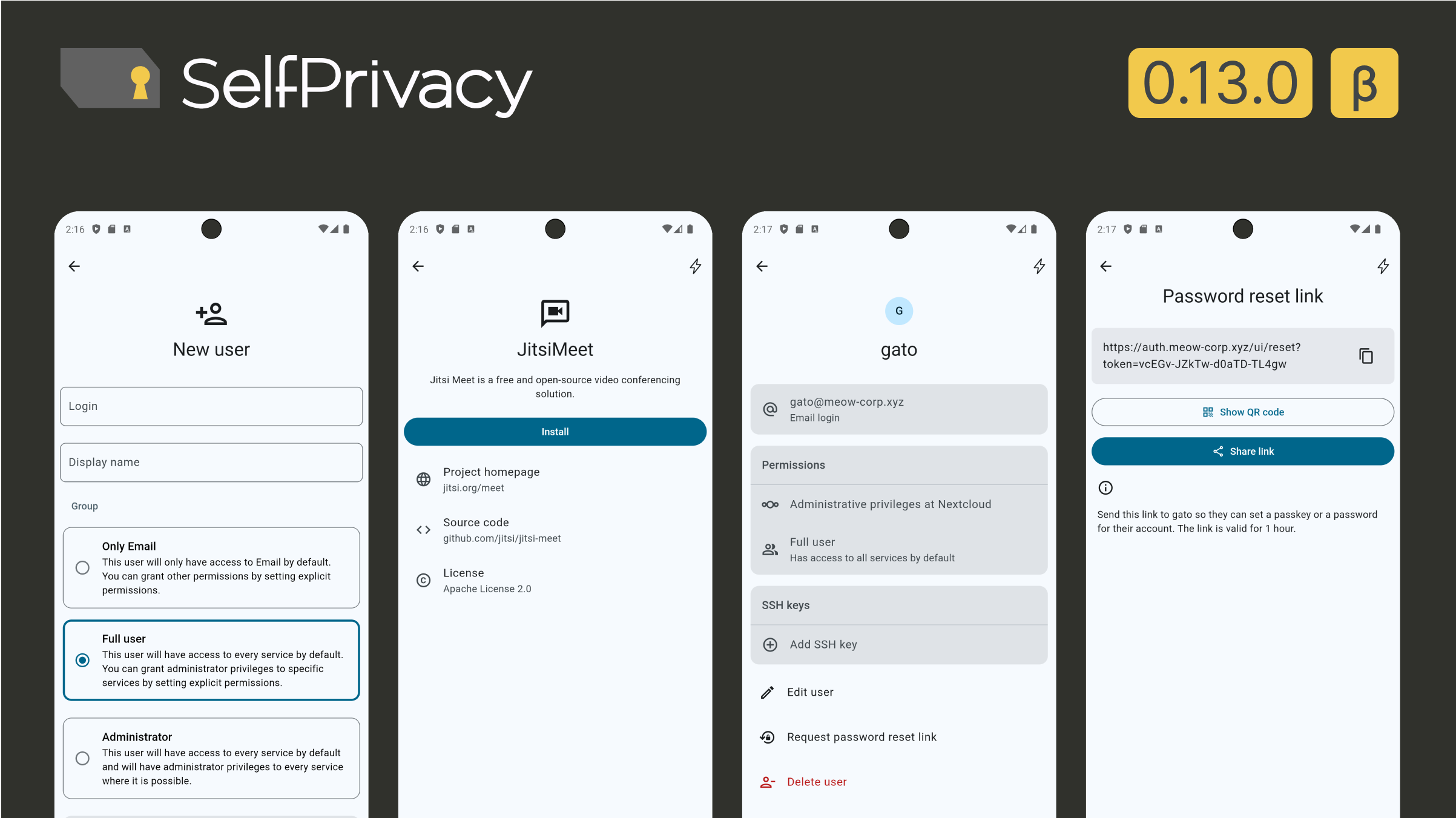
This release finally brings Single Sign On to SelfPrivacy!
Important: after upgrading to a new release, upgrade your server and fix DNS records using the app. Without it, SSO won’t work.
Single Sign On is a feature that allows your users to login into different services on your SelfPrivacy server using a single account. And you, as an administrator, get the centralized user management.
We use Kanidm as an Identity Management server.
Right now, the following services in SelfPrivacy support SSO:
Single Sign On will be turned off by default on existing servers, except for E-mail.
Because E-mail clients do not usually support SSO mechanisms, we provide a Self-Service Portal for your users, where they can manage their E-mail passwords. To not interrupt your current processes, we migrate an existing password to the new system as an E-mail password. It means, it can only be used to log in an E-mail client.
To use other services with SSO:
Further down in the post we will discuss the caveats related to turning on SSO in each service.
At api. subdomain of your server, there will be a self-service portal for your users. Right now, it has the following functions:
Your E-mail server will support both oAuth2 and plain logins. The existing user password will be migrated as an E-mail password, so your E-mail clients should continue working as usual. You will still need to use the full E-mail (with domain) as a username to log in.
After you enable SSO:
After you enable SSO:
You will have to use SSO login instead of username and password.
Now, when you create (or edit) a user, you will see two new inputs: group and explicit permissions.
Group determines implied permissions of a user, and there are three of them:
Explicit permissions override a group permission on a service-by-service level. Admin permission includes user access.
After you create an account for a user, they need to set credentials. It is something they should do themselves. Use the “Request password reset link” button to generate a link. A new screen will give you the options to copy link, share it or show a QR code of it.
Clicked by an accident? No worries. Credentials are not changed until a user visits a link. This link is only valid for an hour.
Estonian
German
Italian
Japanese
Russian
This release is made possible with the support of NLnet foundation
Enabled the following languages:
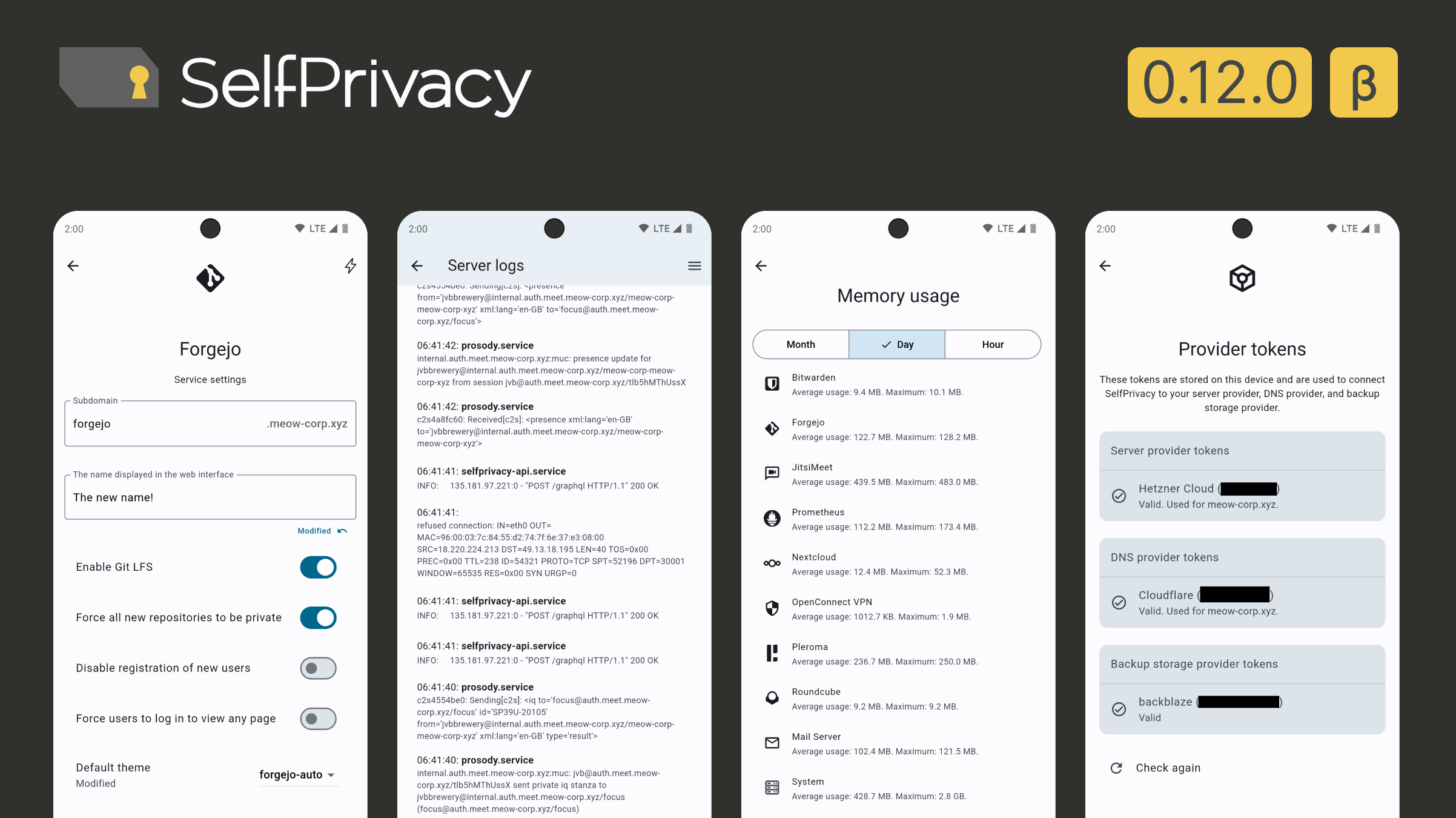
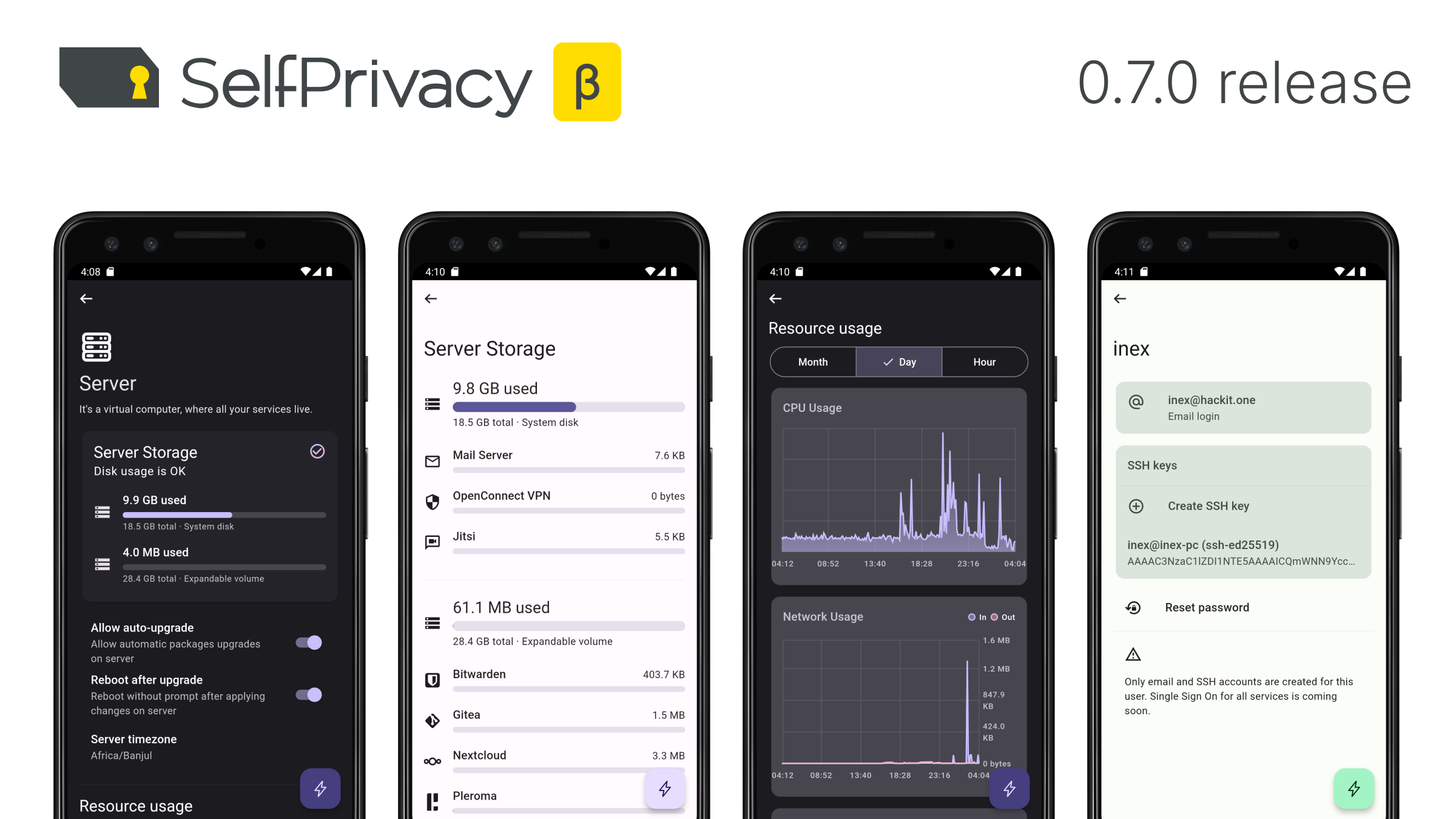
Monitoring: You can now view CPU, Network and RAM stats from the server (#532)
Recovery: You can now skip the server provider token during recovery (#532, a step towards resolving #450)
Recovery: Allow setting the provider token after the recovery (#532)
Providers: You can now view the provider tokens status (#532)
UI: Add a notification if the app doesn’t support the server API version (#531)
Services: Allow viewing service logs from the service screen (#532)
Services: Service settings (#531)
Update DNS records after actions that potentially require DNS changes (#531, resolves #523)
Use Websockets to update server jobs status (#529, resolves #522)
UI: Allow selecting text from Markdown articles (#524, resolves #470)
Console: Obscure auth headers from console logs (#482)
Jobs: Implement NixOS garbage collection job (#506)
UI: List Tiles now have a circular border. (#482, resolves #463)
Settings: Added language picker to the settings (#482, resolves #489)
UI: Show the error screen when secret storage fails to load (#504)
Console: Added an empty view when there are no logs in console yet. (#482, resolves #492)
Backups: Show how much space a service uses on backup (#500, resolves #434)
Installation: Add country names to installation process (#501, resolves #494)
Console: Reworked app console. (#482)
UI: Infobox draws itself in a single row if there is enough space. (#482)
Services: You can now copy a link on the service page (#461, resolves #452)
Services: You can now open the service screen by tapping the service disk usage card (#446)
Installation: Remove the “I already have a server” button after starting the installation (#497, resolves #414)
Polish
Ukrainian
Estonian
Japanese
Kazakh
Russian
Belarusian
Russian
Estonian
This release contains a fix for a security vulnerability. We recommend updating as soon as possible.
UnblvR discovered that the application used an insecure random number generator. This could allow an attacker to predict the random numbers generated by the application, which could lead to a variety of security issues.
While we believe the risk of exploitation is low, we recommend that you update the token on your original device:
Only the token of the initial device might be vulnerable. Tokens of other devices and backups encryption key are generated by your server with a secure random number generator.
Servers created with this version and newer will not be vulnerable to this.
We would like to thank UnblvR for the responsible disclosure of the vulnerability.
Estonian
German
Russian
Estonian
Italian
Japanese
Russian
Slovenian
Enabled the following languages:
Server management: Add ssh settings (#477)
UI: Server settings is now a separate screen (#477)
UI: The new About page now contains links to our support channels (#464, resolves #339 and #170)
Jobs: Now you can track the result of jobs, and the progress of the server rebuilds and upgrades (#440, resolves #254)
UI: On iOS, use the Curpentino bottom navbar (#483)
UI: Use Curpentino widgets where possible on iOS (#483)
Jobs: Block starting client-side jobs when the server is rebuilding or moving a service (#477)
UI: On the bottom bar, show all labels, not only the selected one (#458, resolves #454)
UI: Move provider card titles to the top row (#449, resolves #448)
Unified management of API connection to the server: the app should be now more reactive to changes (#440)
UI: Onboarding page now looks better on big screens (#444)
Kazakh
Chinese (Simplified)
Polish
Russian
Hebrew
Estonian
Thai
German
Ukrainian
Arabic
French
Spanish
German
Hebrew
Russian
This release is made possible with the support of NlNet foundation
XDG_DATA_HOME storage path on Linux for app data (#240)Ukrainian
Latvian
German
Thai
Polish
Slovenian
Czech
Russian
Slovak
Macedonian
Belarusian
French
Spanish
Azerbaijani
We’ve introduced a new system to control where your services’ data is stored, but an initial migration is needed. Without it, you won’t be able to move services between volumes.
We highly encourage you to manually back up your data from the server before migrating.
To use the new disk management features properly you have to perform the migration. Go to the “More” tab and tap on the “Start migration” button. This migration is also known as “binds migration” in our internals, and you may see this term if you encounter an error related to this system. If you do, please report it to us, and we will help.
From now on, our app also deployed on our own F-Droid repository, allowing you to get our builds faster.
https://fdroid.selfprivacy.org
This repository contains two apps: SelfPrivacy and SelfPrivacy Nightly. The first one contains release builds, and the second one is for development builds. They may contain bugs, but will allow you to test our new features before release. All three Android builds (Official F-Droid, our own F-Droid and Nightly) are independent and can be installed simultaneously.
You can also try out our experimental desktop builds, available for Linux as Flatpak, Windows and macOS. https://git.selfprivacy.org/kherel/selfprivacy.org.app/releases/tag/0.7.0 Please keep in mind that we cannot guarantee that the app will launch on your distro, and that we have not adapted our UI for desktops yet.
SelfPrivacy aims to make self-hosting accessible to non-technical users. Born out of a dream to enable every person on the internet to live free of Big Tech surveillance, it provides a simple solution to set up and manage your own server.
Welcome to the NGI Zero podcast, where we talk to the people who are building the next generation internet.
Hi, I'm Ronnie Lam.
And I'm Tessel Renzenbrink.
We're both from NLnet, a foundation which supports people who are working on a free and open internet.
Our guests today are Kirill Zholnay and Inex Code.
Kirill is the founder of LoRaType, a text messenger device using LoRa radio to communicate so you can chat independent of the internet. He's also the founder of SelfPrivacy, the project funded by NGI Zero we will be speaking about today.
Inex Code is the lead full-stack engineer at SelfPrivacy.
SelfPrivacy is a free application that helps you set up and manage your self-hosted services. The goal is to create an accessible tool that gives everyone the opportunity to create their own self-hosted infrastructure.
Hi Kirill and Inex, welcome.
Hello everybody, how are you?
If we talk about the internet, what are the key issues that you see today with the internet?
Oh, I am mature enough to remember the internet in the 2000s. Back then it was academic and decentralized, not commercial and centralized. It was about sharing information and not controlling users. Big tech didn't track your every move. Today the biggest problem is lack of privacy and it's getting worse. On the bright side, the European Union has improved things with GDPR, but it's unclear how well big tech is following the rules.
As a system engineer, I think even if you ask your data to be deleted, it will remain in backups and cold storage. There are also negative trends such as chat control.
And how does SelfPrivacy contribute to addressing those issues?
When ordinary users realize they are being tracked, they seek ethical services. Not so bad, they switch to another big tech company, maybe more ethical, but still centralized like Matrix, Signal, Proton, Tuta. In the best case, they discover open source self-hosting, but it's too hard to set up and maintain these services securely. Even for experienced IT professionals, we make self-hosting painless. SelfPrivacy's main goal is to enable ordinary users to own their private services without relying on big tech.
And how do you offer this service? What does it look like?
In IT terms, our project is like Ansible and Terraform combined into an easy-to-use app. Users simply sign up to the same service providers that professional system admins use. It's virtual server providers, DNS servers, and backup storage.
SelfPrivacy is not a service provider. We don't have any information about or access to the user's server. We know nothing about them. Our application is basically a set of scripts that set up, configure, and update user's server.
Okay, and so I was looking at it, and I really like the idea of having a lot of support from you to set up the self-hosting. And you tell me, as a system engineer, that you will not be able to see my data or my credentials, but how do I, as a non-technical person, know that it's true? You say you work with zero trust, but how can I verify that you don't know my stuff?
Inex, do you want to say something?
It's an interesting question. First of all, we don't have any access to your server. Our application doesn't send any information to us. While the server downloads from our server the configuration for the server, the module is to set up all the services. These are all the same for everyone. If you have the skills to check the NixOS code, you can read it.
Yeah, so even if I personally can't check it, I can ask somebody who understands, who can read the code, to check it for me?
Yes, like everywhere in the open source.
You can remove our application and use your server without us. You can update your server manually if you want. You don't need SelfPrivacy for it.
Yeah, thanks. That answers my question.
You just mentioned [NixOS](https://nixos.org/). Can you tell me a bit more about the NixOS ecosystem?
NixOS is a declarative operating system based on the [package manager Nix](), which allows us to declare all the system configuration and service configuration in one place. As it is powered by a Nix programming language, we were able to adapt the single configuration to address the needs of different users.
We have a single Nix config, which loads the data of the user, like which services users want to launch, which configuration values does the user want, and using Nix language, we can modify the system without modifying the Nix files themselves on the user's machine. There are a lot of projects that are like ours. They try different approaches. There are projects like YunoHost. They use Debian installation scripts and stuff like this, like in the usual style of how things on Linux are done.
There are projects that use Docker, Kubernetes, and other container systems. And when the project started, we saw that and we tried to do this using NixOS. Because initially, SelfPrivacy was a hackathon project, so we tried to do this with Kubernetes, and it ended up badly.
So, as I know, we are the only project that tries to achieve this goal using Nix, and it is not easy. As for now, we see that if we try to use different approaches that are used by other projects, in many ways, it will be easier to implement, but advantages of using NixOS came out to be quite dramatic for us. And we are still sticking to this.
We are trying to do stuff that wasn't done yet in this ecosystem. I think we are doing quite good at this.
Shortly, we hate Docker and Kubernetes.
We hear that a lot.
How do you handle updates? As a user, do I need to log in to the server itself? Or will that be done from the app front-end?
There are two options. If you have automatic updates enabled, your server will update itself every day. If you disabled automatic updates, you will have to open the app and click a big shiny button, update server. And that's it. You will see the progress with the recent updates that we will release this week. You will see in real time the process of NixOS rebuilds.
And that also handles major revisions of NixOS?
Could you please repeat?
And that also handles major revisions of NixOS like 23.11 to 24.05?
Well, previously, major releases of NixOS were such a pain for us because we had to switch channels. And it's not something you can quite automatically do with a single predetermined command. And in the previous year, we moved to using Flakes. And this allowed us to actually pin not just channel, but commit in the Nix packages. And now we may actually push updates of the new major releases.
The problem was that when a new major NixOS release comes out, there are incompatible changes in the configuration that must be addressed. And before, when the channel and configuration updates were separate, they were out of sync, and it caused problems. Now, as our configuration itself pins a NixOS version, we can update them at the same time. And nowadays, when you click update, it will just update to a new version.
It's clearly for end user.
We hide this from the user, well, because user doesn't really need to know about this, like these technical details. We just made it so you click a button and it updates.
Yeah, nice. And also, the setup is also very nice, that you handle it from an app on your phone, and the rest is being done automatically.
Can you tell us something about working on this project? What is hard about working on it?
First of all, our technology stack is complex. NixOS, Flutter, Dart, Python, GraphQL. Inex tell me more.
Well, that's a lot of technologies. And NixOS is quite niche. It's hard to find specialists in this field. And our needs with NixOS are quite advanced. So, the hardest part here was to find people who are capable enough to actually implement our needs in the Nix language.
How to implement different features such as single sign-on and others declaratively in Nix?
How do we integrate everything? One of the most difficult tasks is also integrating everything.
We have three layers. It's the Nix layer, where we have our configuration. We have API layer, which connects the system itself with the application, which modifies the Nix inputs. And the application itself is also quite complex.
Second, the mission is challenging. We are creating automated cloud hosting for non-technical users. And third, the other one is political. I am Russian by birth, was in Ukraine before the war. And now I am in Germany. Jetzt lerne ich Deutsch. Our team of six people is based in Georgia. It's difficult.
Talking about that, can you tell us something as to why you started making SelfPrivacy?
I was amazed by the high level of privacy when I first saw [DeltaChat](https://delta.chat/). DeltaChat is my crush.
Sorry, one moment. Can you explain what is DeltaChat for people who don't know?
Improvise. He has better English.
In a nutshell, DeltaChat is an email client, which behaves like a messenger, which also encrypts all the messages end-to-end. And it also allows group chats, and all the messages are encrypted. And it has quite a nice UX, UI.
But the only way to achieve full privacy for DeltaChat is for both parties to use their own email servers. That was four years ago. There is still no easy way for non-technical users to set up their own mail server. SelfPrivacy does this in a few clicks and gives you unlimited email addresses for the cost of VPS. It's around 5 euros per month.
And why do you think it is important to give non-technical users this possibility?
They have no way to do it privately. I think only us. If you want an email server, what should you do?
Well, you might contact other people who can set up the server, but do you trust them? Is it private?
There are email server providers which will do it for you for money, but all your data is handled by them. Do you trust them?
You likely do not trust.
That's a very good reason.
So earlier we talked about what the hard parts are of working on this project, but can you also tell me something that you really like about it?
Oh, we enjoy reading feedback, like "it just works", "it's magic". It's very motivating. Many people know the difficulty of setting up an email server and getting the DNS setting correct. *We just make it work.*
That's really nice.
Yeah, I like the zero trust model that you use, and also, I mean, you are creating a communication channel for people that do not trust other servers, other companies, and especially not the Signal and the Telegrams of this world. One thing that I was thinking is, do you also use an encrypted file system on the server? Because it might be possible. One of the options that you offer through Hetzner, for example, is that those companies look into the server and read the files that are in there. Or am I now describing a feature request?
Currently, users can choose Hetzner or DigitalOcean as their VPS provider. However, we plan to add [Proxmox](https://www.proxmox.com/en/) as a bare-metal server to increase independence and security. And then you can edit the encryption for the file system.
I might also add that this is a feature request that we received, and we thought about it a lot. So the problem here is, for example, if we encrypt a virtual machine on Hetzner, they might just dump the operating memory and extract the keys. So this encryption only protects the data at rest. So it actually won't protect anything, and you still have to trust the provider.
So that's why we are working on allowing you to set up SelfPrivacy on any provider or at your home. And only after that, we will add new providers to our application.
For full privacy, you should use a dedicated server.
Yeah, true.
You're also working together with or making use of deSEC.io, which is also another NLNet-funded project. Why did you choose them, and how does that work out for you?
I say, but maybe Inex repeats more correctly. Firstly, we are using Cloudflare because they have a DNS API. Nobody has it, but NGI told me about deSEC, and we are happy to use it. Inex, could you repeat correctly?
Well, quite a lot of DNS providers have DNS API.
They are not ethical. We are not sure they don't collect information.
It is not ethical either, but we used it because it is only a DNS, so no user data actually passed through it. And it is really used because of the ease of its API.
At first, when it was SelfPrivacy was a prototype, so it was the first one that was supported, and then we added deSEC because we wanted a more private alternative, and we knew that it was also NLNet-funded. It was also the reason we chose it. And it was lucky for us that deSEC also has an API, and it works well with our application. And in the future, we are planning to add many more DNS providers, but it will take some time.
If you have an ethical VPS provider, we will be happy.
Is running or having DNS inside the SelfPrivacy server, is that something that is or might be on the roadmap?
We had talks about it, and it might be possible, but it's harder to implement. And here is a chicken and egg problem. How do we stop access to the server when it is not yet created? We still need DNS records to access it because we use TLS, encrypted connections, and we need a domain for that.
What you might do, then, is use the initial hostname that is being set by the VPS provider.
Well, not every provider actually provides it. And the server also needs to actually learn this address somehow from itself and acquire TLS certificates for it. There are technical difficulties with this. Maybe it is possible to implement, but it is not in our priorities currently. Our current priority is to add more DNS providers and implement other features right now.
It is not private. Upstream traffic can read.
They can read the DNS requests?
Requests, yeah.
What is your target audience? What people do you have in mind that should be using SelfPrivacy?
My dream is everybody use family servers for a loved one. I am not a businessman. I am a bad marketing guy. I am just technical. I see the problem and I know how to fix it with technical possibilities.
Well, you are not entirely a bad marketing guy because I looked at your website and it is very clear. It is kind of funny, I think. And it has these really nice cartoons on it. Who made those?
It is our designer, Nevfy. She is awesome. It is so young and so cool.
It is presented really nice and as I said, it also really explains what SelfPrivacy does.
We are not sure. Even IT guys don't understand what we are doing and why. I don't know why. It is because we are here.
Talking about business, what steps are you taking to ensure the longer-term sustainability of your projects?
I think about it every time. This project is expensive for me. I spent a lot of money and time for it but I didn't see an ethical way to monetization. We don't want to be engaged with a service provider because it is not zero trust. We don't want to know our clients.
Maybe we can create a subscription in the marketplaces. For example, Google Play Market We tried to publish our software to the Apple Store but we were banned or something else. Nobody responded to us. But I want SelfPrivacy free always for Android users. It's very critical.
Maybe we can add a commercial project in the SelfPrivacy-like platform. For example, some data analytics. I don't know. Now we have a platform for any open-source software which allows NixOS. And I like that. If you have some business mentor I will be happy to speak with them.
Actually, we do. The NGI Zero Coalition also offers practical support. One of those supports is organizations like Apple or CCT they offer mentor support for business models. We could definitely help you with that.
Awesome.
And did you think about a donation model?
I don't believe that. I know nobody who can earn with donation. Maybe I have a lack of information. But I know one. It was... If you know [TOGAF ArchiMate](https://www.opengroup.org/archimate-forum/archimate-overview) program it's enterprise architecture software and they can live on donation.
If I understand correctly you are basically funding this yourself, right?
Yeah.
You're paying people to develop it.
Yeah, I'm paying every week. For Georgia it's fine. It's impossible to do in Europe. Europe is too expensive.
So you have other businesses where you earn the money and then you just put it into SelfPrivacy?
Yeah, you're right.
That's true dedication.
It is, yeah. And I can also recommend doing some donation model putting a donation button on your website because I'm very sure that there are donors out there that really believe in privacy and would like to fund you.
Okay, thank you. But I need help with it. And I'm afraid that Google banned us because Google don't like donation on the site.
Google doesn't like it when you put links or use payments outside of the Google system. So we might add it to the Android flavor donation button. But speaking with Google Play, maybe it will be easier just to make an application paid in the Google Play and free in the F-droid like, for example, OsmAnd does.
Yeah. What are the next steps for SelfPrivacy?
At the moment, SelfPrivacy offers services such as email, video meetings, password management and file server. We are planning to add more communication and collaboration services in particular Fediverse services such as [PeerTube](https://joinpeertube.org/), [Mastodon](https://joinmastodon.org/) and [Castopod](https://castopod.org/).
What I really like about that list of projects is that you are choosing truly open-source projects. Yeah, that's an amazing list.
I might say that *we add services that we use ourselves* because we all are self-hosters with a large experience. Me, for example, I self-host for years already and I know all the pain of setting everything up on different systems how it is actually not always easy to maintain everything.
It might be easy to set up something but maintaining is a chore and sometimes it is not a chore you actually want to do. But you have to, because, for example, there are security advisories, there are updates that you have to apply, you run out of space, something is down, you have to up this and sometimes it's just sad seeing all of this.
What can the listeners of our podcast do to help you to bring your project further?
Just install SelfPrivacy, communicate with your loved ones via DeltaChat, and escape big tech surveillance. Send me a nice message on DeltaChat if you want. When I want to speak with someone I want to send an email to the private server. I have a private server. I want everyone to have a private server.
That's really nice. Can you tell us something about how NGI Zero helped your project?
NGI Zero has been a lot of help. First of all, *it's confirmation that we are doing the right thing*. When I look at other projects that NGI has supported, I feel that there is still hope for privacy on the Internet.
Can you give advice to people who are also considering to apply for NGI Zero?
Be brave. Apply and don't be afraid to discuss your ideas. Your idea could be a breakthrough. It could change everything for the better. Unfortunately, many IT professionals are too shy.
That's beautiful advice. To go back to the start of this conversation we asked you both what are the issues today with the Internet. You are giving a slice of the solution by creating and maintaining SelfPrivacy. Do you see any other initiatives or trends that are contributing to improving the Internet a bit?
Maybe I'm too pessimistic. So far, all I can see is that privacy is getting worse. I've also heard that NGI might have funding problems but I hope for the best and we will continue to develop SelfPrivacy as much as I can.
If we are to solve the problems of privacy on the Internet what should be done? What would be the fundamental steps that would improve it?
Inex?
My first thought is that it's educating people about privacy, about their data, about how the data is processed, what can be done with it. Because *Big Tech did a great job at educating people of their own paradigm*. It is hard for people to move to actually private services. Federated protocols are very confusing for ordinary people. We see a lot of problems people have, things like choosing a server, what server do I have to choose? What is a server anyway? And a lot of people... I'm not sure about places like Germany. I heard that in Germany people really like privacy. But in other places it is a common thing to hear, like "I don't have anything to hide!" It's hard to actually change this mind usually, from the people.
NGI has supported a lot of great independent initiatives. The best thing you can do is keep doing this for the long term and make the Internet healthier.
Yeah, I think that's a good combination of solutions. On the one hand to educate the end users and on the other hand make the Internet actually better so that they have something to choose from. It's really good advice. Thank you. Do you have any more questions, Ronny?
No, I think this was a wonderful conversation about a very interesting project.
Thank you. I can end it. There would be no room for conflict if the world could exchange ideas without being watched. People can all agree on anything when there is no asymmetry of access to information.
That's beautiful. That's a beautiful way to work towards. Well, thank you Kirill and Inex very much for this great conversation and even more for the SelfPrivacy project that you are working on because it's really contributing to a better Internet for all. Thank you very much.
Thank you.
Thank you.
Большое спасибо!
The SelfPrivacy project was granted NGI funding via NLnet. Other FOSS related projects also benefit from NGI funding. This funding is now at risk for future projects.
Initially publishead by petites singularités. English translation provided by OW2.
Open Letter to the European Commission.
Since 2020, Next Generation Internet (NGI) programmes, part of European Commission’s Horizon programme, fund free software in Europe using a cascade funding mechanism (see for example NLnet’s calls). This year, according to the Horizon Europe working draft detailing funding programmes for 2025, we notice that Next Generation Internet is not mentioned any more as part of Cluster 4.
NGI programmes have shown their strength and importance to supporting the European software infrastructure, as a generic funding instrument to fund digital commons and ensure their long-term sustainability. We find this transformation incomprehensible, moreover when NGI has proven efficient and economical to support free software as a whole, from the smallest to the most established initiatives. This ecosystem diversity backs the strength of European technological innovation, and maintaining the NGI initiative to provide structural support to software projects at the heart of worldwide innovation is key to enforce the sovereignty of a European infrastructure. Contrary to common perception, technical innovations often originate from European rather than North American programming communities, and are mostly initiated by small-scaled organizations.
Previous Cluster 4 allocated 27 million euros to:
In the name of these challenges, more than 500 projects received NGI funding in the first 5 years, backed by 18 organisations managing these European funding consortia.
NGI contributes to a vast ecosystem, as most of its budget is allocated to fund third parties by the means of open calls, to structure commons that cover the whole Internet scope - from hardware to application, operating systems, digital identities or data traffic supervision. This third-party funding is not renewed in the current program, leaving many projects short on resources for research and innovation in Europe.
Moreover, NGI allows exchanges and collaborations across all the Euro zone countries as well as “widening countries” 1, currently both a success and an ongoing progress, likewise the Erasmus programme before us. NGI also contributes to opening and supporting longer relationships than strict project funding does. It encourages implementing projects funded as pilots, backing collaboration, identification and reuse of common elements across projects, interoperability in identification systems and beyond, and setting up development models that mix diverse scales and types of European funding schemes.
While the USA, China or Russia deploy huge public and private resources to develop software and infrastructure that massively capture private consumer data, the EU can’t afford this renunciation. Free and open source software, as supported by NGI since 2020, is by design the opposite of potential vectors for foreign interference. It lets us keep our data local and favors a community-wide economy and know-how, while allowing an international collaboration. This is all the more essential in the current geopolitical context: the challenge of technological sovereignty is central, and free software allows addressing it while acting for peace and sovereignty in the digital world as a whole.
*1 As defined by Horizon Europe, widening Member States are Bulgaria, Croatia, Cyprus, the Czech Republic, Estonia, Greece, Hungary, Latvia, Lituania, Malta, Poland, Portugal, Romania, Slovakia and Slovenia. Widening associated countries (under condition of an association agreement) include Albania, Armenia, Bosnia, Feroe Islands, Georgia, Kosovo, Moldavia, Montenegro, Morocco, North Macedonia, Serbia, Tunisia, Turkey and Ukraine. Widening overseas regions are : Guadeloupe, French Guyana, Martinique, Reunion Island, Mayotte, Saint-Martin, The Azores, Madeira, the Canary Islands.